- Asa Firepower Active Directory Integration
- Azure Active Directory Authentication
- Cisco Asa Active Directory Authentication
In this Cisco ASA tutorial, IT author-speaker Don R. Crawley shows you how to configure a Cisco ASA Security Appliance to support integration with Active Directory for VPN user authentication. Active Directory and Kerberos Cisco ASA can authenticate VPN users via an external Windows Active Directory, which uses Kerberos for authentication. Kerberos is an authentication protocol created by the Massachusetts Institute of Technology (MIT) that provides mutual authentication used by many vendors and applications.
Most often we Cisco-guys uses radius or tacacs when we are about to do authentication of users. But did you know that doing authentication from VPN to a user-database in an Active Directory doesn´t require IAS, ACS or any third party software at all. In fact there are multiple ways in ASA to talk to AD built-in.
I have tried them in my home lab by using an ASA firewall and a Windows 2003 Server with Active Directory installed.
I am looking at purchasing a Cisco ASA 5510 - Question re EZVPN Capabilities.can i base acl's for fine grained control on active directory groups? I know i can tie in for authentication using IAS, but would like to have network access for dial in users based on AD group membership rather than maintained on the firewall itself. My previous article looked at directly integrating Active Directory (AD) with ASA for VPN authentication using LDAP. Taking that to the next step, this article looks at using Active Directory.
LDAP
aaa-server LDAP protocol ldap
aaa-server LDAP (outside) host 192.168.1.51
ldap-base-dn CN=Users,DC=kvistofta,DC=local
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *
ldap-login-dn CN=admin,CN=Users,DC=kvistofta,DC=local
server-type microsoft
Verification:
FW(config)# test aaa authen KERBEROS host 192.168.1.51 username vpnuser passwo$
INFO: Attempting Authentication test to IP address <192.168.1.51> (timeout: 12 seconds)
INFO: Authentication Successful
FW(config)# test aaa authen LDAP host 192.168.1.51 username vpnuser password 1$
INFO: Attempting Authenticatio
[75] Session Start
n test to IP address <192.168.1.51> (timeout: 12 seconds)
[75] New request Session, context 0xd5954260, reqType = 1
[75] Fiber started
[75] Creating LDAP context with uri=ldap://192.168.1.51:389
[75] Connect to LDAP server: ldap://192.168.1.51:389, status = Successful
[75] supportedLDAPVersion: value = 3
[75] supportedLDAPVersion: value = 2
[75] Binding as administrator
[75] Performing Simple authentication for admin to 192.168.1.51
[75] LDAP Search:
Base DN = [CN=Users,DC=kvistofta,DC=local]
Filter = [sAMAccountName=vpnuser]
Scope = [SUBTREE]
[75] User DN = [CN=vpnuser,CN=Users,DC=kvistofta,DC=local]
[75] Talking to Active Directory server 192.168.1.51
[75] Reading password policy for vpnuser, dn:CN=vpnuser,CN=Users,DC=kvistofta,DC=local
[75] Read bad password count 0
[75] Binding as user
[75] Performing Simple authentication for vpnuser to 192.168.1.51
[75] Processing LDAP response for user vpnuser
[75] Authentication successful for vpnuser to 192.168.1.51
[75] Retrieved User Attributes:
[75] objectClass: value = top
[75] objectClass: value = person
[75] objectClass: value = organizationalPerson
[75] objectClass: value = user
[75] cn: value = vpnuser
[75] givenName: value = vpnuser
[75] distinguishedName: value = CN=vpnuser,CN=Users,DC=kvistofta,DC=local
[75] instanceType: value = 4
[75] whenCreated: value = 20100706114926.0Z
[75] whenChanged: value = 20100706114926.0Z
[75] displayName: value = vpnuser
[75] uSNCreated: value = 13726
[75] uSNChanged: value = 13731
[75] name: value = vpnuser
[75] objectGUID: value = .1..O.c.v..
[75] userAccountControl: value = 66048
[75] badPwdCount: value = 0
[75] codePage: value = 0
[75] countryCode: value = 0
[75] badPasswordTime: value = 0
[75] lastLogoff: value = 0
[75] lastLogon: value = 129228917453688826
[75] pwdLastSet: value = 129228905663476095
[75] primaryGroupID: value = 513
[75] objectSid: value = .......LP..r{..'S..
[75] accountExpires: value = 9223372036854775807
[75] logonCount: value = 5
[75] sAMAccountName: value = vpnuser
[75] sAMAccountType: value = 805306368
[75] userPrincipalName: value = vpnuser@kvistofta.local
[75] objectCategory: value = CN=Person,CN=Schema,CN=Configuration,DC=kvistofta,DC=local
[75] Fiber exit Tx=547 bytes Rx=2053 bytes, status=1
[75] Session End
INFO: Authentication Successful
FW(config)#
KERBEROS
aaa-server KERBEROS protocol kerberos
aaa-server KERBEROS (outside) host 192.168.1.51
kerberos-realm KVISTOFTA.LOCAL
Verification:
FW(config)# test aaa authen KERBEROS host 192.168.1.51 username vpnuser passwo$
INFO: Attempting Authentication test to IP address <192.168.1.51> (timeout: 12 seconds)
kip_lookup_by_sessID: kip with id 76l not found
Kerberos library reports: 'Additional preauthentication required'
INFO: Authentication Successful
FW(config)#
NT Domain
aaa-server NT (outside) host 192.168.1.51
nt-auth-domain-controller kvistofta
Verification:
FW(config)# test aaa auth NT host 192.168.1.51 username vpnuser password 1qaz!$
INFO: Attempting Authentication test to IP address <192.168.1.51> (timeout: 12 seconds)
smb_iod_request :
smb_iod_process_message :
smb_iod_negotiate : iod_state = No connect
smb_iod_negotiate : tcreate
smb_iod_negotiate : bind
smb_iod_negotiate : tconnect
smb_iod_addrq :
smb_iod_sendrq : iod_state = transport active
smb_iod_waitrq :
smb_iod_removerq :
smb_iod_negotiate : completed
smb_iod_process_message :
smb_iod_thread : going to sleep for 2 secs 0 nsecs
smb_iod_process_message :
smb_iod_thread : going to sleep for 2 secs 0 nsecs
smb_iod_request :
smb_iod_process_message :
smb_iod_ssnsetup : iod_state = unknown stat(3)
smb_iod_addrq :
smb_iod_sendrq : iod_state = unknown stat(4)
smb_iod_waitrq :
smb_iod_removerq :
smb_iod_ssnsetup : completed
smb_iod_process_message :
smb_iod_thread : going to sleep for 2 secs 0 nsecs
smb_iod_process_message :
smb_iod_thread : going to sleep for 2 secs 0 nsecs
Connected to VPNUSER
smb_iod_request :
smb_iod_process_message :
smb_iod_addrq :
smb_iod_sendrq : iod_state = session established
smb_iod_waitrq :
smb_iod_removerq :
smb_iod_process_message :
smb_iod_thread : going to sleep for 2 secs 0 nsecs
smb_iod_request :
smb_iod_process_message :
INFO: Authentication Successful
FW(config)#
Posted in Uncategorized
KB ID 0000685
Problem
Note: The procedure is the same for Server 2016 and 2019

This week I was configuring some 2008 R2RADIUS authentication, so I thought I’d take a look at how Microsoft have changed the process for 2012. The whole thing was surprisingly painless.
I will say that Kerberos Authentication is a LOT easier to configure, but I’ve yet to test that with 2012, (watch this space).
Solution
Step 1 Configure the ASA for AAA RADIUS Authentication
1. Connect to your ASDM, > Configuration.
2. Remote Access VPN.
3. AAA Local Users > AAA Server Groups.
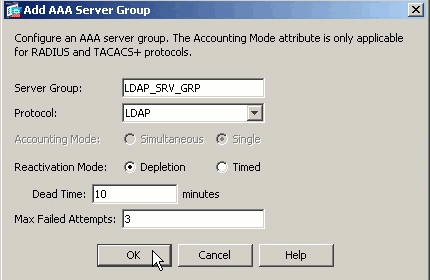
4. In the Server group section > Add.
5. Give the group a name and accept the defaults > OK.
6. Now (with the group selected) > In the bottom (Server) section > Add.
7. Specify the IP address, and a shared secret that the ASA will use with the 2012 Server performing RADIUS > OK.
8. Apply.
Configure AAA RADIUS from command line;
Step 2 Configure Windows 2012 Server to allow RADIUS
9. On the Windows 2012 Server > Launch Server Manager > Local Server.
10. Manage > Add Roles and Features.
11. If you get an initial welcome page, tick the box to ‘skip’ > Next > Accept the ‘Role based or feature based installation’ > Next.
Autocad 2011 cd key changer. For example, installing AutoCAD 2011 as a point product requires product key 001C1, but installing AutoCAD 2011 from the AutoCAD Revit Architecture Suite 2011 requires product key 241C1. The same version of AutoCAD is in both software packages but the.
12. We are installing locally > Next.
13. Add ‘Network Policy and Access Server’ > Next.
14. Add Features.
15. Next.
16. Next.
Asa Firepower Active Directory Integration
17. Next.
18. Install.
19. When complete > Close.
20. Select NPAS (Server 2016), or NAP (Server 2012).
21. Right click the server > Network Policy Server.
22. Right click NPS > Register server in Active Directory.
23. Expand RADIUS > right click RADIUS clients > New.
24. Give the firewall a friendly name, (take note of what this is, you will need it again) > Specify its IP > Enter the shared secret you setup above (number 7) > OK.
25. Expand policies > right click ‘Connection Request Policies’ > New.
26. Give the policy a name > Next.
27. Add a condition > Set the condition to ‘Client Friendly Name’ > Add.
28. Specify the name you set up above (number 24) > OK > Next.
29. Next.
30. Next.
31. Change the attribute to ‘User-Name’ > Next.
32. Finish.
33. Now right click ‘Network Policies’ > New.
34. Give the policy a name> Next.
35. Add a condition > User Groups.
36. Add in the AD security group you want to allow access to > OK > Next.
37. Next.
38. Access Granted > Next.
39. Select ‘Unencrypted Authentication PAPSPAP” > Next.
40. Select No.
41. Next.
42. Next.
43. Finish.
Step 3 Test RADIUS Authentication
44. Back at the ASDM, in the same page you were in previously, select your server and then click ‘Test’.
45. Change the selection to Authentication > Enter your domain credentials > OK.
Azure Active Directory Authentication
46. You are looking for a successful outcome.
Omnisphere response code. You'll then receive a Response Code, which you'll select with your cursor and copy (Control-C on Windows or Command-C on Mac): 7. Return back to Omnisphere. Click PASTE and the Response Code will now be displayed in Omnisphere. Now remove Omnisphere from your host sequencer. Re-insert Omnisphere into your host. Spectrasonics omnisphere response code serial numbers, cracks and keygens are presented here. No registration is needed. Just download and enjoy. Spectrasonics Omnisphere - Dvd6 key code generator: Spectrasonics Omnisphere 2008 patch: Spectrasonics Omnisphere.
Note: if it fails check there is physical connectivity between the two devices, the shared secrets match. Also ensure UDP ports 1645 and 1646 are not being blocked.
To Test AAA RADIUS Authentication from Command Line
Cisco Asa Active Directory Authentication
47. Finally, save the firewall changes > File > Save running configuration to flash.
Related Articles, References, Credits, or External Links
