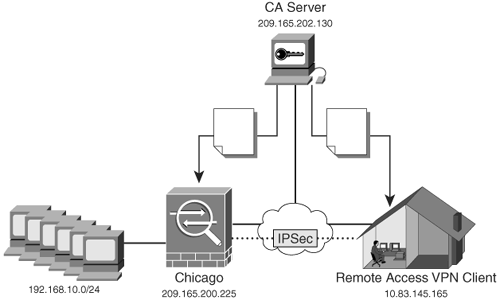
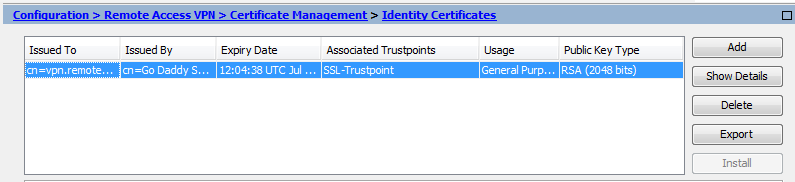
1) Assume that the PEM certificate is good and try to get the Default-RSA-Key copied from the ASA to the correct directory on the Windows 2003 Server, then run certutil.exe to repair the store and match the private key to the certificate. 2) Revoke the ASA's working certificate, generate a private key on the Windows 2003 Server, request a new certificate for the same domain name and install it on IIS, then export the pair to the ASA. If the keysize is largen than 2048 bits, the certificate can not be used for securing the the webssl/anyconnect. ASA currently does not support 4096 bit keys (Cisco bug ID CSCut53512) for SSL server authentication. However, IKEv2 does support the use of 4096 bit server certificates on the ASA 5580, 5585, and 5500-X platforms alone. Once the certificate has been imported on the ASA is possible to export the certificate and private key used on the CSR. Is important to backup the identity certificates in case a hardware/software failure. To backup the identity certificates thought ASDM we go to the path: ConfigurationRemote Access VPNCertificate ManagementIdentity Certificates.
Unlike Cisco IOS routers, which by default don't allow RSA private keys to be exported from NVRAM, Cisco ASAs don't protect private keys. But there's no command (of which I'm aware) to directly export the keys either.Sometimes you need to squirrel away those keys. You can do it by getting a certificate that uses the keys, then exporting a certificate bundle (with private key included). Here's how.
First, create a key:
Next, create a trustpoint which references the key, and generate a self-signed certificate:
Now the
 throwaway trustpoint has a certificate. Export that certificate to the terminal.
throwaway trustpoint has a certificate. Export that certificate to the terminal.Save the blob of text including the begin/end lines. The blob is a PKCS12 bundle encrypted using the passphrase above and then base64 encoded. Be sure to save the encryption passphrase.
We no longer need the certificate or the throwaway trustpoint in which it's stored. Kill it. The private key will survive.
The easiest way to get the key onto an ASA is to import the PKCS12 blob using the passphrase. Importing the certificate will create 3 things on the ASA:
- The RSA keypair
- The certificate
- A trustpoint to hold the certificate
Now the key is available for use, but there's a useless certificate and trustpoint as well. Kill those off just like before. The key will survive.
Another option is to extract the key from the PKCS12 bundle using openssl on some other device. First, save the text blob without the BEGIN/END lines to a file. I'd probably call it throwaway.p12.base64. Then, it needs to be base64-decoded, and parsed from a pkcs12 certificate bundle into a pem-formated private key. The private key output contains both the private and public keys.
The example above was run on MacOS, where the base64 binary has BSD heritage. On Linux, use -d rather than -D with the GNU flavor of base64.
Cisco export and contract compliance
Cisco products, software, and technology (Cisco products) are subject to export controls under the laws and regulations of the United States (US), the European Union (EU), and any other applicable countries’ export laws and regulations. Export, re-export, transfer, and use of Cisco products may require obtaining US and local authorizations, permits, or licenses.
Cisco products are controlled under the US Export Administration Regulations and Wassenaar Arrangement as telecommunications/networking equipment in category 5 part 2. The classification of Cisco’s Products and CCATs can be retrieved from Cisco's Public Export Product Data Tool.
Cisco products may not be exported or re-exported to embargoed destinations: Cuba, Iran, North Korea, Sudan, Syria, and the Crimea Region. Cisco products may not be delivered to individuals or entities listed on the US government Denied/Restricted Parties List or other applicable countries of export without first obtaining a license.
Cisco products may not be used directly or indirectly for uses inconsistent with its original design and intended application (e.g., communications and network management).
As a US company is obliged to comply with the US anti-boycott laws and refuse to participate in foreign boycotts that the United States does not sanction.
Exporters, distributors, customers, and users of Cisco Products are responsible for compliance with US and local country export/Import laws and regulations.
US AND EU export control laws and regulations
In the US, the export, re-export, and in-country transfer of controlled goods, software, and technology (dual-use items) are controlled by a branch of the US Department of Commerce known as the Bureau of Industry and Security through the Export Administration Regulations (EAR).
In the EU, the export of dual-use items are controlled under EU Regulation 428/2009, setting up a community regime for the control of exports, transfer, brokering, and transit of dual-use items.
US and EU export restrictions for Cisco products
In the case of Cisco products containing encryption, Cisco reviews all of its products prior to export and classifies them in accordance with the US Export Administration Regulations (EAR) well in advance of a product's release date.
Once a review has been completed, products may become eligible for a particular license exception, such as ENC, and this exception may then be used by other exporters, as provided by EAR.
Cisco solutions and products containing encryption less than 56 bits (80 bits in the US); unrestricted products may be exported and re-exported to most civilian, commercial, and government end users under License Exception ENC (15 CFR Part 740.17(b)(1) or 740.17(b)(3) of EAR) located in all territories, with the exception of embargoed destinations and countries designated as supporting terrorist activities. The countries listed in Part 746 of EAR as embargoed destinations requiring a license are: Cuba, Iran, North Korea, Sudan, Syria, and the Crimea Region.
Cisco's encryption solutions and products containing encryption greater than 56 bits--80 in the US--(also referred to as restricted products) have undergone a one-time review by the US government and may be exported or re-exported under License Exception ENC (15 CFR Part 740.17(b)(2) of EAR) to most civilian, commercial, and less sensitive government end users (for definition see part 772 of EAR) located in all territories except the embargoed destinations and countries designated as supporting terrorist activities (i.e. Cuba, Iran, North Korea, Sudan, Syria, and the Crimea Region).
Exports and re-exports to more sensitive government entities (see part 772 EAR) not located in the following countries may require a US export license in order to obtain restricted encryption items: Australia, Austria, Belgium, Bulgaria, Canada, Croatia, Cyprus, Czech Republic, Denmark, Estonia, Finland, France, Germany, Greece, Hungary, Iceland, Ireland, Italy, Japan, Latvia, Lithuania, Luxembourg, Malta, Netherlands, New Zealand, Norway, Poland, Portugal, Romania, Slovakia, Slovenia, Spain, Sweden, Switzerland, Turkey, United Kingdom, and the United States.
Under EU export control laws, both restricted and unrestricted encryption solutions and products can be exported within the EU to EU member states, but exports from the EU outside of the EU may require a license.
Mass market products normally do not require a license under US, EU and most local laws (except when exporting to embargoed destinations). Mass market products are exported from the US under the designation “No License Required” (NLR). Free safe halloween screensavers.
Cisco Asa Product Line
All transactions must undergo a compliance check to ensure that none of the parties to an order are listed on any applicable sanctioned or denied entity list. Please review the US Bureau of Industry and Security's Lists of Parties of Concern.
Military and defense (International Traffic in Arms Regulations [ITAR]). No Cisco products are regulated by the ITAR.
Further information
The US Commerce Department's Bureau of Industry and Security Website provides US export guidance at https://www.bis.doc.gov/index.php/regulations/commerce-control-list-ccl.
Cisco Asa Software
Non-US and US companies re-exporting Cisco products or technology must comply with both their local export regulations and with the US re-export regulations. Guidance regarding re-exports and other offshore transactions involving US origin items can be found at https://www.bis.doc.gov/index.php/licensing/reexports-and-offshore-transactions.
The EU Commission provides information about the EU export control regulations at https://ec.europa.eu/trade/import-and-export-rules/export-from-eu/dual-use-controls/.
Cisco Asa Models
Further guidance published by some EU member states can be found at:
